
GCHQ boss Jeremy Fleming revealing the first details of a British cyberattack in 2018
Credit: PA
Against this background of an intensifying global cyber conflict, it seems inevitable that attacks like the one disclosed by Fleming in Manchester are set to become more frequent.
Around the world, governments and businesses are grappling with a rising tide of cyberattacks mounted by a plethora of groups — from criminal gangs to highly organised hacker groups backed by nation states including Russia, Iran and China. Increasingly, western governments are hitting back to defend their interests and to serve as a deterrent.
This year hackers from Russia, China and North Korea even targeted UK Covid vaccine research programmes, underscoring Britain’s willingness to declare its intent and ability to strike back where necessary.
For a decade now, offensive cyber operations have been quietly deployed by security agencies to disrupt the ambitions of hostile countries.
Arguably the first major significant operation targeted the Natanz Nuclear Facility in Iran in 2010. Experts believe US and Israeli operatives injected Stuxnet, a malicious piece of software code, into the operation of uranium enrichment centrifuges at the site. The operation caused them to spin out of control, seriously hampering the country’s push to develop nuclear weapons.
In fact, the Natanz attack was so effective it may have backfired, by triggering a cyber arms race in which western adversaries including Iran, North Korea and others have rushed to develop and use similar techniques — at far lower cost than conventional military programmes.
Over the past decade, a growing number of countries have been honing their own offensive cyber capabilities and launched state-sponsored hacking attacks.
“When I first started in this business there were only a handful of nations that had any decent capabilities,” says Tony Cole, the chief technology officer of cybersecurity business Attivo Networks. “Today around 75 nations have some significant capability.”
Attackers follow a familiar playbook. First, they will carefully scan for vulnerabilities in an enemy’s infrastructure such as power plants, military bases and government offices. Once they have found a way into the network, they use specialist software to slip inside, steal documents or wreak havoc by inserting malicious code and then leave again.
Russian hacking incidents
One of the big appeals of the new offensive capabilities being developed by western governments is their potential to serve as a deterrent. A Russian hacking group might think twice about stealing vaccine research from Oxford University if they knew that the National Cyber Force had succeeded in breaking into the gang’s own servers, for example.
The UK’s new hacking force signals that security chiefs are now taking offensive cyber operations more seriously. It could lead to a wave of attacks on foreign targets — a prospect which alarms some experts who fret about the implications.
Not everyone believes the UK’s new National Cyber Force represents a step change in the country’s capabilities. Three security sources said the establishment of the new hacking force may simply be a bureaucratic exercise designed to ease longstanding tensions between the military and security services over such capabilities.
“It’s one of two things,” says one security source. “It’s just a nice, announceable reorganisation of deck chairs with the military around current posture or it’s a significant expansion of aggressive posture in cyberspace. I don’t think it’s the latter.”
Either way, the rapid rise of cyber conflict is prompting a growing number of ethical questions.
Broadly speaking, offensive cyberattacks can be split into three different categories. The first — peacetime attacks against ransomware groups and foreign hacker groups — are unlikely to generate tremendous controversy. Similarly, attacks undertaken during wartime against an adversary’s military infrastructure are considered fair game. If you’re at war in Syria and want to hack into the country’s radar system, that’s viewed as acceptable.
But an awkward middle ground also exists including an attack on an adversary’s domestic infrastructure during peacetime. Is it ethical or legal, for example, to hack into a North Korean power station which supplies energy for both civilian and military purposes?
These grey areas worry experts who believe more debate is needed over offensive cyber operations in the UK.
“The legal questions are pretty significant and pretty clear cut about it not being lawful and ethical to shut down the power grid in Moscow, for example, because of the potentially severe impact that would have,” says Joseph Devanny, a lecturer in national security studies at King’s College London.
If the UK escalates the tempo of cyberattacks it undertakes then it could also risk accidentally overstepping the mark and launching an attack that could be considered an open act of war.
Countries that are launching government-backed hacking attacks
“Offensive cyberattacks may formally and practically amount to the use of force and the level of armed aggression,” says Dr Lukasz Olejnik, an independent cybersecurity consultant.
“What matters is the effects achieved with the cyberattack,” he continues. “Do they amount to paralysing disruption, destruction, or prolonged irreversible effects? The useful rule of thumb is achieving effects that are roughly similar to those reached with a potential kinetic attack.”
So if a cyberattack gets out of hand and accidentally shuts down a power grid, the UK could face serious international repercussions.
“You don’t want to do things that will cut the power supply to a hospital or jam the entire function of a city where people will freeze to death and will have no cashpoints working,” says a security source. “The Government is not likely to be consciously reckless in terms of suddenly launching attacks taking out power supplies to hospitals.”
A second security insider says hacking other countries during peacetime can be complicated. “GCHQ has always had the authority to do this under UK legislation, subject to lawful authorisation. But this involves careful calculations about possible intelligence access loss as well as judgements about what will actually have an impact and for how long.”
There’s also an increasing concern that stockpiling cyberweapons and vulnerabilities in popular software can be disastrous if those tools leak out.
The US’s powerful National Security Agency suffered the theft of some of its top cyber-weapons in 2016, while last week FireEye, a highly regarded US cybersecurity business, revealed that it had been hacked by a suspected Russian group which made off with similar highly specialised software.
The devastating WannaCry attack in 2017 which shut down organisations around the world was carried out by North Korea using the very NSA hacking tools which had been stolen the previous year.
Deciding to use hacking tools on a foreign military base means you risk that country gaining access to the software and repurposing it. “What you have to remember with cyber weapons is when you use them, they’re done,” says Joseph Carson, the chief security scientist at Thycotic. “Others can reprogramme and use them against you.”
The UK announcement of a new hacking force provided a welcome PR push at the end of 2020, but experts caution against blindly escalating the number of cyberattacks without a proper debate over the ethics.
“I think offensive cyber is dangerously under-scrutinised,” says one security source. “And it’s all because of this deliberately created mystique around it. The presumption should be the normal scrutiny applied to defence capabilities and that is not where we are at the minute.”

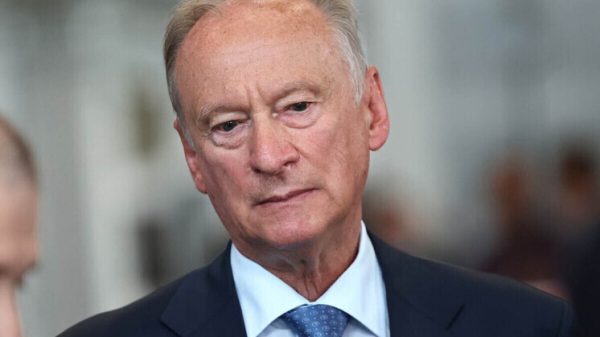




















































Свежие комментарии